10 Windows Event Log Best Practices You Should Know
Learn the best mix of Windows Event log practices
- Only logging event logs isn't sufficient as you need to extract information from them.
- You should have all the information you need from a log to mitigate the issue.
- Read this guide to understand the best Windows Event log practices that you should follow.
You need to ensure that the event logs that you note give you the right information about the network health or attempted security breaches, because of advancements in technology.
While organizations are trying to apply best practices for Windows Event logs, they still fail to formulate a security-focused monitoring policy.
In this guide, we will give you 10 of the best practices for Windows Event Log that will help you address any adverse challenges in your network. Let us get right into it.
Why is applying the best Windows Event log practices essential?
Event logs contain important information about any incident that happens on the internet. This includes any security information, login or logoff activity, unsuccessful/successful access attempts, and more.
You can also know about malware infections or data breaches using the event logs. A network admin will have real-time access to track the potential security threats and can immediately take action to mitigate the occurring issue.
Moreover, many organizations have to maintain Windows Event logs to comply with regulatory compliance for audit trails, etc.
What are the best Windows Event log practices?
- Why is applying the best Windows Event log practices essential?
- What are the best Windows Event log practices?
- 1. Enable auditing
- 2. Define your audit policy
- 3. Consolidate log records centrally
- 4. Enable real-time monitoring and notifications
- 5. Make sure to have a log retention policy
- 6. Reduce events clutter
- 7. Make sure that the clocks are synchronized
- 8. Design logging practices based on your company's policies
- 9. Ensure the log entry has all information
- 10. Use efficient log monitoring and analysis tools
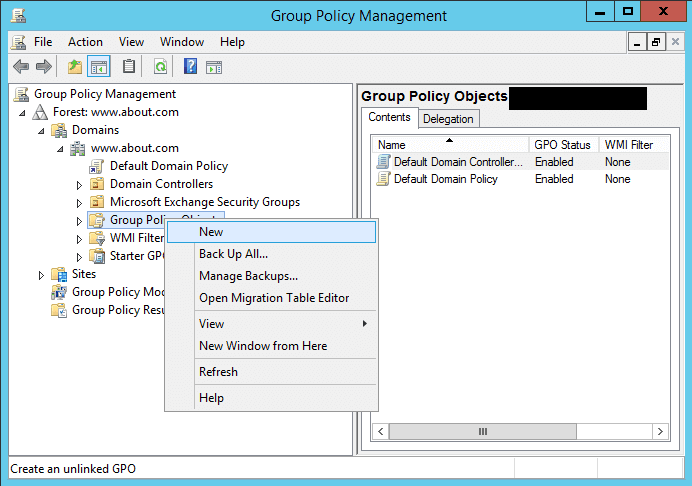
1. Enable auditing
In order to monitor the Windows Event log, you need to first enable auditing. When auditing is enabled, you will be able to track user activity, login activity, security breaches or other security events, etc.
Simply enabling auditing isn’t beneficial, but you have to enable auditing for system authorization, file or folder access, and other system events.
When you enable this you will get granular details about the system events and can troubleshoot based on the event information.
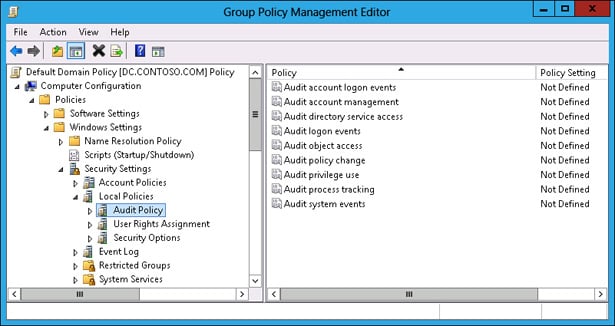
2. Define your audit policy
Audit policy simply means that you have to define what security event logs you want to record. After announcing compliance requirements, local laws and regulations, and incidents that you require to log, you will multiply the benefits.
The major benefit would be that your organization’s security governance team, legal department, and other stakeholders will get the required information to tackle any security issues. As a general rule, you need to set the audit policy by hand on individual servers and workstations.
3. Consolidate log records centrally
Do note that Windows event logs aren’t centralized, meaning that each network device or system is recording events in its own event logs.
To get a broader picture and help mitigate the issues quickly, network admins need to find a way to merge the records in the central data for complete monitoring. Furthermore, this will help in monitoring, analysis, and reporting much easier.
Not only consolidating log records centrally will help but it should be set to be done automatically. As the involvement of a large number of machines, users, etc. will complicate the collection of the log data.
4. Enable real-time monitoring and notifications
Many organizations prefer using the same type of devices all across along with the same operating system, which is most commonly Windows OS.
However, network administrators, may not always want to monitor one type of operating system or device. They might want flexibility and the option to choose more than just Windows event log monitoring.
For this, you should opt for Syslog support for all systems including UNIX and LINUX. Moreover, you should also enable real-time monitoring of logs and ensure that each polled event is recorded at regular intervals and generates an alert or notification when it is detected.
The best method would be to establish an event monitoring system that records all events and configure a higher polling frequency. Once you get hold of the events and the system, you can then chalk out and dial down the number of events that you wish to monitor.
5. Make sure to have a log retention policy
Only collecting logs centrally doesn’t mean much in the longer run. As one of the best Windows event log practices, you should make sure to have a log retention policy.
When you enable a log retention policy for longer periods, you will get to know the performance of your network and devices. Moreover, you will also be able to track data breaches and events that happened over time.
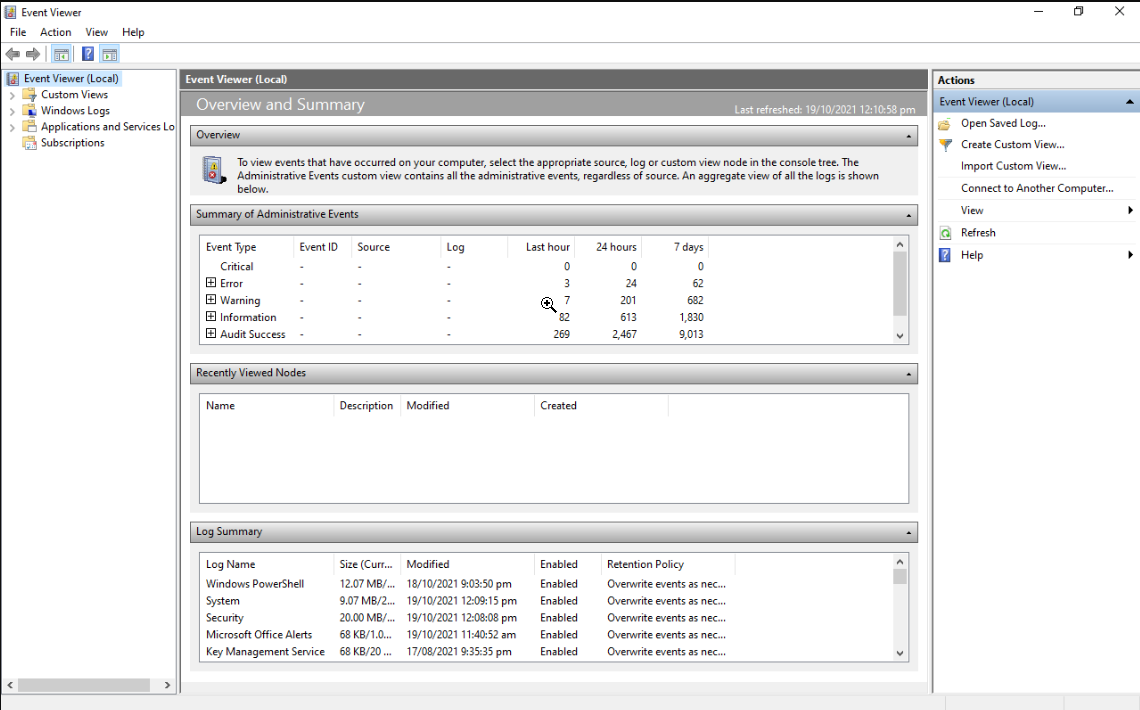
You can tweak the log retention policy using the Microsoft Event Viewer and set the maximum security log size.
6. Reduce events clutter
While having logs of all events is a great thing to have in your arsenal as a network admin, logging too many events can also take your attention away from the one that is important.
You may overlook the critical information and it may lead to security breaches bypass. In such a case, you should carefully audit your security policy and as one of the best Windows Event log practices, we would suggest you log only critical events.
7. Make sure that the clocks are synchronized
While you have set the best policies to track and monitor the Windows Event logs, it is essential that you have synchronized clocks across all of your systems.
One of the essential and best Windows Event log practices that you can follow is to make sure that clocks are synchronized across the board to make sure you have the correct time stamps.
Even if there is a small discrepancy in time among the systems, it will result in harder monitoring of events and could also lead to security lapse in case the events are diagnosed late.
Make sure that you check your system clocks weekly and set the correct time and date to mitigate security risks.
8. Design logging practices based on your company’s policies
A logging policy and the events that are logged is an important asset to any organization to troubleshoot network issues.
So, you should make sure that the logging policy that you have applied goes in line with the company’s policies. This could include:
- Role-based access controls
- Real-time monitoring and resolution
- Apply the least-privilege policy when configuring resources
- Check logs before storing and processing
- Mask sensitive information that is important and crucial to an organization’s identity
9. Ensure the log entry has all information
The security team and administrators should come together to build a logging and monitoring program that will ensure that you have all the information required to mitigate attacks.
Here is the common list of information that you should have in your log entry:
- Actor – Who has a username and an IP address
- Action – Read/write on which source
- Time – Timestamp of the event occurrence
- Location – Geolocation, code script name
The above four pieces of information constitute the who, what, when, and where information of a log. And if you know the answers to these crucial four questions, you will be able to properly mitigate the problem.
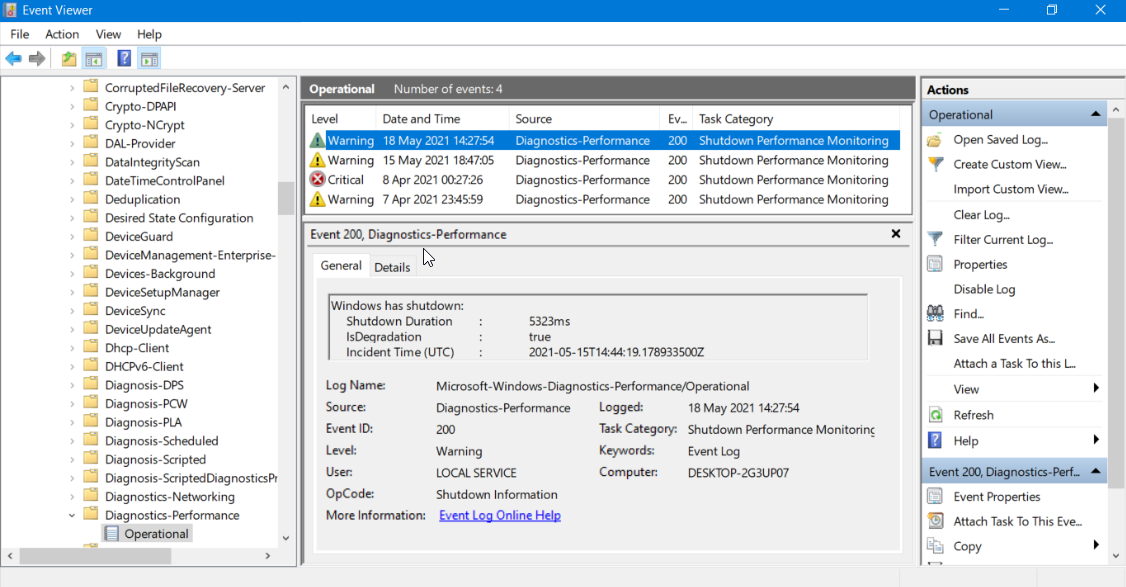
10. Use efficient log monitoring and analysis tools
Manually troubleshooting the event log isn’t that foolproof and can also prove to be a hit and a miss. In such a case, we would suggest you make use of logging monitoring and analysis tools.
For your convenience, we have a guide that lists some of the best event log analysis tools that you can use. The list contains free and advanced analysis tools.
Moreover, you can check out our list of the best log monitoring software for Windows 10 and 11 to automate and get a helping hand in tackling issues.
That is it from us in this guide. We have a guide that explains in detail how you can fix the Event Viewer not working in Windows 10 and 11 problems.
Feel free to let us know in the comments below, which set of the best Windows Event log practices are following from the above list.